
By: Joseph Ross
When was the last time you bought an album on a CD? On a vinyl? On a cassette? When was the last time you listened to that physical copy of that album?
Today, many people would have to think long and hard about the answer to these questions. That’s because music is changing, and music consumption is changing along with it. Streaming services, such as Spotify, Apple Music, and Tidal, have become the predominant way many people listen to music. In the United States alone, 77% of all music was listened through music streaming services.[1]
The number of people subscribing to music streaming services is increasing at a rapid speed. In 2015, there were roughly 77 million subscribers to streaming sites, while in 2019 this number rose to 304 million.[2] Spotify went from 18 million subscribers in the beginning of 2015 to 124 million subscribers by the end of 2019.[3] Apple music also saw a substantial increase in subscribers over this period, going from just under 10 million subscribers in 2015 to 68 million subscribers by the end of 2019. [4]
This increase in streaming service subscriptions has been a major factor in the decline of physical album sales. In 2020, physical album sales fell below 1 million for the first time since Nielsen Music/MRC Data began keeping track in 1991.[5] The previous low for physical album sales was the prior week, highlighting the trend of decrease in physical album sales. [6]
Streaming has not made listening to music any less popular, however. In fact, just the opposite. Music consumption is increasing yearly, with total on demand streams up 35%.[7] Because of this, the music industry has had to update their music listening metrics. Recently, the Recording Industry Association of America changed their methodology by which albums are certified gold and platinum. The RIAA now includes streaming in this process in an attempt to modernize the process.[8]
One possible reason that streaming has become so popular over the last half decade is the freedom of selection it offers its listeners. Listeners of the past used to have to buy whole albums just to listen to the few songs that they like. This has completely changed. Now with streaming services, a listener can choose to go to an album but only listen to the few songs that they enjoy. Take, for example, popular rapper Drake’s last album, Scorpion, which was one of the most popular albums of the 2018. It consisted of 25 songs, but 63% of the streams came from only three songs.[9] And Drake was not the only artist this happened too. Pop star Post Malone, on his latest album beerbongs & bentley’s, saw over 60% of his streams also come from just three songs.[10] Music listeners today have the ability to just listen to the songs they like, rather than having to buy an entire album.
So, what are the new measurements? Under the new structure 150 streams of one song equals one paid download and ten paid downloads is equal to one album download.[11] This means that an artists album will have to be streamed 1,500 times on a streaming service for an album sale to be counted. An album or song needs to be streamed on one of the approved streaming platforms.[12] This includes video platforms such as YouTube as well as on-demand sites like Spotify and Apple Music.[13] One way the sales number did not change was it continues to not count radio plays. This means when a song is played on the radio, or a radio service platform such as Pandora or iHeartRadio, these streams do not affect the album or song sales numbers.[14]
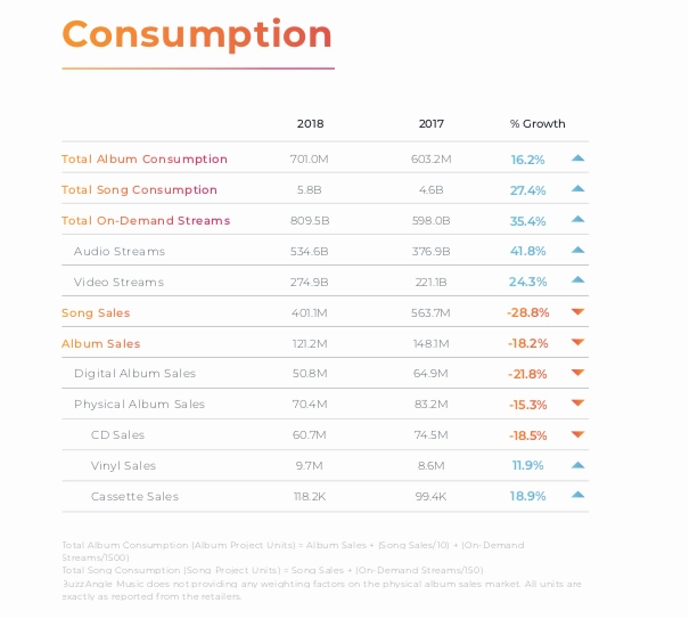
Even as streaming becomes the dominant way in which people listen to music, it hasn’t completely killed off every physical form of albums. Vinyl sales have seen a resurgence over the last few years. Vinyl sales account for over 15% of all physical album sales.[15] There are several reasons for this. One reason is the sound quality of vinyls, which many feel is superior to digital audio.[16] Possibly the biggest reason is people like their retroness![17] According to one study done by MusicWatch, nearly half of all current vinyl buyers are under the age of 25.[18] Some people (myself included) enjoy collecting these old vinyls. The resurrection of vinyls provides some hope that maybe other forms of physical albums will also become popular again one day.
Citations:
Hugh McIntyre, Now That Streaming Can Make an Album, What Counts and What Doesn’t?, Forbes (Feb. 13, 2016, 08:45am), https://www.forbes.com/sites/hughmcintyre/2016/02/13/now-that-streaming-can-make-a-song-platinum-what-counts-and-what-doesnt/#2664beb617ef
Amy X. Wang, Album Sales Are Dying as Fast as Streaming Services Are Rising, Rolling Stones (Jan. 3 2019, 5:11pm), https://www.rollingstone.com/pro/news/album-sales-dying-as-fast-as-streaming-services-rising-774563/
Tim Ingham, The Album Is in Deep Trouble – and the Music Business Probably Can’t Save it, Rolling Stone (Nov. 9, 2018 1:53pm), https://www.rollingstone.com/music/music-features/the-album-is-in-deep-trouble-and-the-music-business-probably-cant-save-it-753795/
Keith Caulfield, Album Sales Hit New Weekly Low in U.S. – But There Is a Bright Spot, Billboard (Mar. 27, 2020), https://www.billboard.com/articles/business/chart-beat/9345214/us-album-sales-hit-new-low
Ted Goslin, Five Reasons Vinyl is Making a Comeback, Yamaha Music USA (Aug. 24, 2018), https://hub.yamaha.com/five-reasons-vinyl-is-making-a-comeback/#:~:text=Sound%20Quality.,formats%20used%20by%20streaming%20services.
Amy Watson, Streaming Music Subscribers Worldwide 2015-2020, Statista (Sep. 9 2020), https://www.statista.com/statistics/669113/number-music-streaming-subscribers/
Amy Watson, Spotify’s Premium Subscribers 2015-2020, Statista(Aug. 21, 2020), https://www.statista.com/statistics/244995/number-of-paying-spotify-subscribers/
Amy Watson, Number of Apple Music Subscribers Worldwide 2015-2019, Statista (July 14, 2020), https://www.statista.com/statistics/604959/number-of-apple-music-subscribers/
[1] Amy X. Wang, Album Sales Are Dying as Fast as Streaming Services Are Rising, Rolling Stones (Jan. 3 2019, 5:11pm), https://www.rollingstone.com/pro/news/album-sales-dying-as-fast-as-streaming-services-rising-774563/
[2] Amy Watson, Streaming Music Subscribers Worldwide 2015-2020, Statista (Sep. 9 2020), https://www.statista.com/statistics/669113/number-music-streaming-subscribers/
[3] Amy Watson, Spotify’s Premium Subscribers 2015-2020, Statista (Aug. 21, 2020), https://www.statista.com/statistics/244995/number-of-paying-spotify-subscribers/
[4] Amy Watson, Number of Apple Music Subscribers Worldwide 2015-2019, Statista (July 14, 2020), https://www.statista.com/statistics/604959/number-of-apple-music-subscribers/
[5] Keith Caulfield, Album Sales Hit New Weekly Low in U.S. – But There Is a Bright Spot, Billboard (Mar. 27, 2020), https://www.billboard.com/articles/business/chart-beat/9345214/us-album-sales-hit-new-low
[6] Id.
[7] Wang, supra note 1.
[8] Hugh McIntyre, Now That Streaming Can Make an Album, What Counts and What Doesn’t?, Forbes (Feb. 13, 2016, 08:45am), https://www.forbes.com/sites/hughmcintyre/2016/02/13/now-that-streaming-can-make-a-song-platinum-what-counts-and-what-doesnt/#2664beb617ef
[9] Tim Ingham, The Album Is in Deep Trouble – and the Music Business Probably Can’t Save it, Rolling Stone (Nov. 9, 2018 1:53pm), https://www.rollingstone.com/music/music-features/the-album-is-in-deep-trouble-and-the-music-business-probably-cant-save-it-753795/
[10] Id.
[11] McIntyre, supra note 8.
[12] Id.
[13] Id.
[14] Id.
[15] Caulfield, supra note 5.
[16] Ted Goslin, Five Reasons Vinyl is Making a Comeback, Yamaha Music USA (Aug. 24, 2018), https://hub.yamaha.com/five-reasons-vinyl-is-making-a-comeback/#:~:text=Sound%20Quality.,formats%20used%20by%20streaming%20services.
[17] Id.
[18] Id.
